![[Go to /]](/DutchGrid-logo-CA.gif)
DCA Root Service
DCA Root CA G1
Trusted Certificate Service TCS
Request your certificate with Academic Login
Guide and tools
Production CA (MS)
Overview
Manage Your Certificates
(for non-TCS users)
Find a local registrar
Classic interface
Help with your request
Host certificate requests
Submit your request
Download your certificate
Renew your certificate
Request revocation
Reliance information
Policy Statement
Reliance Information
NL e-Infra Zero
(training services)
Documentation
Legacy Cert Request Guide
Change a passphrase
RA OpsGuide
OpenSSL for Windows
eToken Guide
Links
EUGridPMA
IGTF
Privacy Policy
| Using the GEANT Trusted Certificate Service TCS for Dutch e-Infrastructures |
|---|
|
URGENT NOTICE: get a new TCS certificate BEFORE APRIL 30!
The TCS service itself is required to periodically tender for a new back-end
provider on the public market. From May 1st, 2020, onwards, the service
will have to rely on a new provider, Sectigo, to produce the
actual certificates. Although the data TCS and GEANT provide remain
the same, Sectigo has not yet been capable of producing compliant
certificates during the testing phase. Recommended actions:
After May 1st, only the Legacy DutchGrid CA may be available to you. We are scaling up capacity and operations to deal with that eventuality, but since the Legacy DutchGrid CA employs air-gapped operations for security reasons, it will always be a slower process. We will be introducing remote vetting procedures and voucher-based upload of documents shortly to address the lack of facsimile machines and applicants now working from home. Such options will be available from April 22nd onwards. However, since the Legacy DutchGrid CA and TCS by design use non-overlapping names, you would have to re-register with your research collaboration membership services or e-infrastructure services. We strongly recommend to get a new DigiCert-based TCS certificate now. |

 The legacy DutchGrid CA is a 'classic' CA
process is not instantaneous: it may take up to a week to complete, and
requires you to visit one of our Registration Authorities in-person.
The legacy DutchGrid CA is a 'classic' CA
process is not instantaneous: it may take up to a week to complete, and
requires you to visit one of our Registration Authorities in-person.
Fortunately, there is a far easier and quicker way to get a certificate
suitable for use on the Grid: the GEANT Trusted Certificate Service TCS,
provided to all Dutch research and academic institutions
through SURFnet, the Dutch Research and Educational Network via the existing connection between your own institution
and SURFconext.
The GEANT TCS is operated by DigiCert, which offers a wider range of certificate types, including "Robot" machine-to-machine certificates, as well as other Grid & Authentication certificates.
| Apply for your certificate now |
In case you need more help or get 'stuck' in the process, try the following:
- Requesting certificates using browsers that lack key generation: FireFox >69, Chrome, and recent Safari's
- Certificate is now in my browser, but I need it in files
- Certificate is in one browser, or in my operating system, but I need it in another one
| Using TCS with Firefox 69+, Chrome, and recent Safari's |
|---|
Since version 69 (September 2019), Firefox is no longer able to generate certificates by itself - this functionality was killed by Mozilla, aligning it with Google Chrome. You can generate your 'certificate request' manually and upload it to the DigiCert SSO portal. You will need OpenSSL for this: it is commonly installed on Linux systems, and downloadable as a binary for Windows and other platforms.
- Generate your keypair and make your electronic request file (which should be protected by a passphrase - don't forget the passphrae chosen here, as you'll need it later in step 4!) in te Globus default location (saving the previous contents if needed):
[ -d $HOME/.globus ] && mv $HOME/.globus $HOME/.globus-backup-saved-on-`date +%Y%m%d-%H%M%S` mkdir $HOME/.globus openssl req -subj "/CN=Pietje Puk 42" -out $HOME/.globus/userrequest.pem -keyout $HOME/.globus/userkey.pem -new chmod 0600 $HOME/.globus/userkey.pem # for Unix systems only cat $HOME/.globus/userrequest.pem
- Login to digicert.com/sso and copy-paste into the request form for "Grid Premium": (click to enlarge)
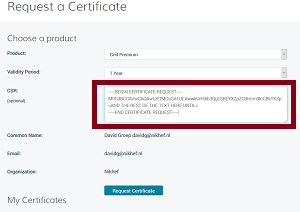
- Download the generated certificate (a ZIP file) from the list (it's the most recent one, sort by clicking the date column heading), download it to e.g. $HOME/Downloads/ and
extract your own certificate to, e.g., $HOME/.globus/usercert.pem. For example:unzip -pqj $HOME/Downloads/*_nl.zip \*_nl.crt > $HOME/.globus/usercert.pem
At this point, use with most e-Infrastructure middleware and grid tools will work.
To register with community membership services, and to use it for authentication to web sites and portals, continue to import it into your browser(s) using a ".p12" (or ".pfx") file here in step 4. - Combine the files into a ".p12" (PKCS#12) file to import in your operating system or browser (using the same passphrase again, actually: three times):
openssl pkcs12 -export -in $HOME/.globus/usercert.pem -inkey $HOME/.globus/userkey.pem -out $HOME/.globus/your-new-packed-cert.p12 chmod 0600 $HOME/.globus/your-new-packed-cert.p12
- On Windows, double-click to import in your OS, or see look at the browser import guide
For Safari, see https://www.digicert.com/kb/ssl-support/p12-import-export-mac-mavericks-server.htm - Verify by visiting https://www.eugridpma.org/your-identity/
curl -o "TCSeSciencePersonalCA3.pem" https://ca.dutchgrid.nl/tcs/TCSeSciencePersonalCA3.pem IMPORTDATE=`date +%Y.%m.%d` openssl pkcs12 -export -in $HOME/.globus/usercert.pem -inkey $HOME/.globus/userkey.pem -certfile TCSeSciencePersonalCA3.pem \ -name "Personal TCS G3 cert of $IMPORTDATE" -out $HOME/.globus/your-new-packed-bundle-on-$IMPORTDATE.p12 chmod 0600 $HOME/.globus/your-new-packed-bundle-on-$IMPORTDATE.p12
| Putting a browser-generated certificate into a file |
|---|
By default, your certificate (and your private key) are located in your browser. You can use this instantly with all web-based services, such as administrative interfaces, VO registration, etc. For use with grid job submission, you should export these to local files on disk, names "usercert.pem" and "userkey.pem", in the following way:
- Open the certificate store of your browser or operating system.
For Apple's MacOS, follow the DigiCert apple export guide.
For Mozilla (the example shown below is Firefox 3), this is located under "Tools", then "Options", "Advanced", and click on "View certificates". In Internet Explorer, go to "Options", "Internte Settings", "Content", and there click "Certificates".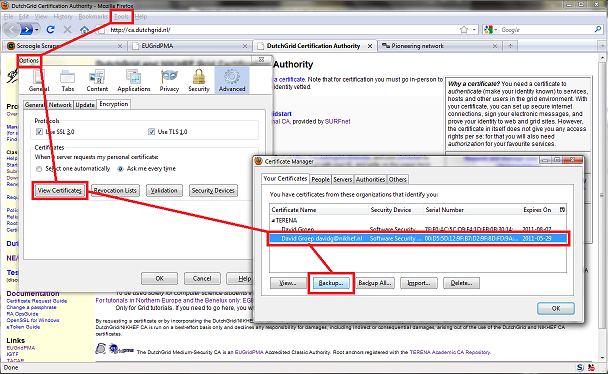
- Click "backup your certificate", and also selet "save private key" when asked for. Store the file (it will be called something.p12, since the file format is called PKCS#12), and remember where you wrote it!
- Start jGridstart and import your
certificate from the PKCS#12 ".p12" file. It is now ready for grid use.
Alternatively, convert the "p12" file to a user cert and user key file using the command-line tools:
openssl pkcs12 -nocerts -in cert.p12 -out $HOME/.globus/userkey.pem openssl pkcs12 -clcerts -nokeys -in cert.p12 -out $HOME/.globus/usercert.pem chmod 0600 $HOME/.globus/userkey.pem chmod 0644 $HOME/.globus/usercert.pemand don't forget the last step (the permissions bit) or you will see strange errors. - Go to the registration page of your user community and join a VO, a 'virtual organisation'. A list of frequently used VOs and how to join them is provided by BiG Grid.
| I have my certificate in one system or browser, but I need it in another |
|---|
You have your certificate in, e.g. Internet Explorer, but you need it in Firefox. Or
in your MacOS keychain. Or vice versa.
The browser in which you can use your certificate holds two elements you need to export:
the certificate itself and the private key. For this reason, you must protect any
intermediate files you create with a passphrase - the browser will ask you for it.
Precise steps differ per browser, but generally include "Export" or "Backup" of the
certificate and private key to a ".p12" or "PKCS#12" file. Once you have
the ".p12 file", import it using "Restore" or by double-clicking on the .p12 file:
| Product | Export | Import |
|---|---|---|
| Internet Explorer & MS Windows |
You can now use the ".pfx" file for import elsewhere. Rename it to ".p12" if needed for other browsers. |
|
| Firefox | To export from Firefox, see the example above - it will give you also the PKCS12 (.p12) file. |
|
| Chrome and Safari | Chrome uses your operating system browser store: in your profile on Windows, or in your Keychain on MacOS. For Windows, use Internet Explorer or certmgr.msc to export. On Apple, use your keychain to backup (export) your certificate and key. |
Chrome uses your operating system browser store: in Windows, double-click on the p12 file and follow the "Internet Explorer" instructions. On MacOS, opening a p12 file will open it in Keychain.
For Apple users, just read this DigiCert guide |
| No access to the TCS service? |
|---|
- Test first by going to www.digicert.com/sso and type (part of) the name of your institution
- No luck finding your organsiation? Ask your institute help desk to request "that the AAI responsible person or SURFnet ICP requests a connection be made to DigiCert in the SURFcontext dashboard and to permit inclusion of the IdP in eduGAIN"
- You find your institution but cannot log in (it complains about missing attributes) but you are an employee? Ask your institute helpdesk to request "that the eduPersonEntitlement to access the TCS, namely urn:mace:terena.org:tcs:personal-user, is set by default for all employees, since they are eligible anyway because the organization keeps a copy of a photo-ID to fulfil the requirements of the 'Wet op de Loonbelasting'"
- Still getting stuck and does your institution need help? Tell them to contact the SURFnet product manager for TCS. You can contact your own organisation by mail at scs-ra@instelling.nl
| For institutions |
|---|
- Background for institutions to configure their identity provider for TCS
- for eScience server certificates ask your regular SURFnet ICP/SCS-RA channels. Just be sure to request Grid SSL Multidomain certs instead of plain UC SSL certs.